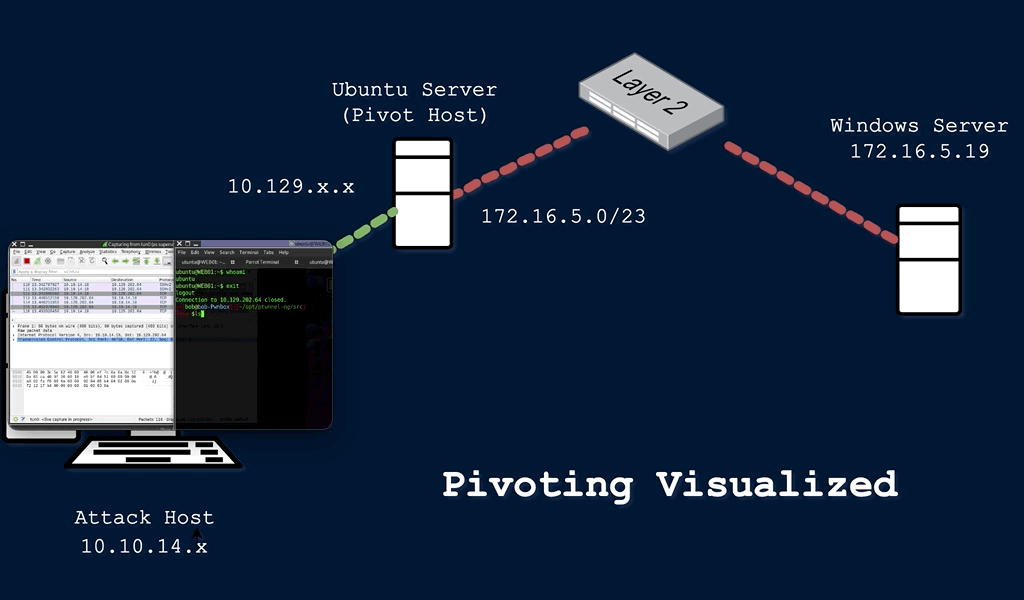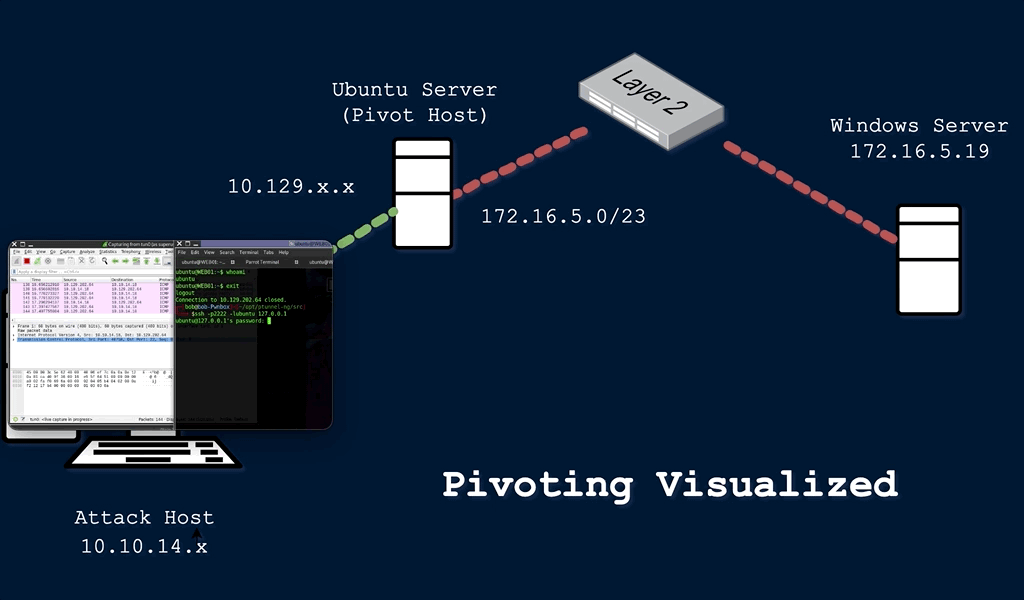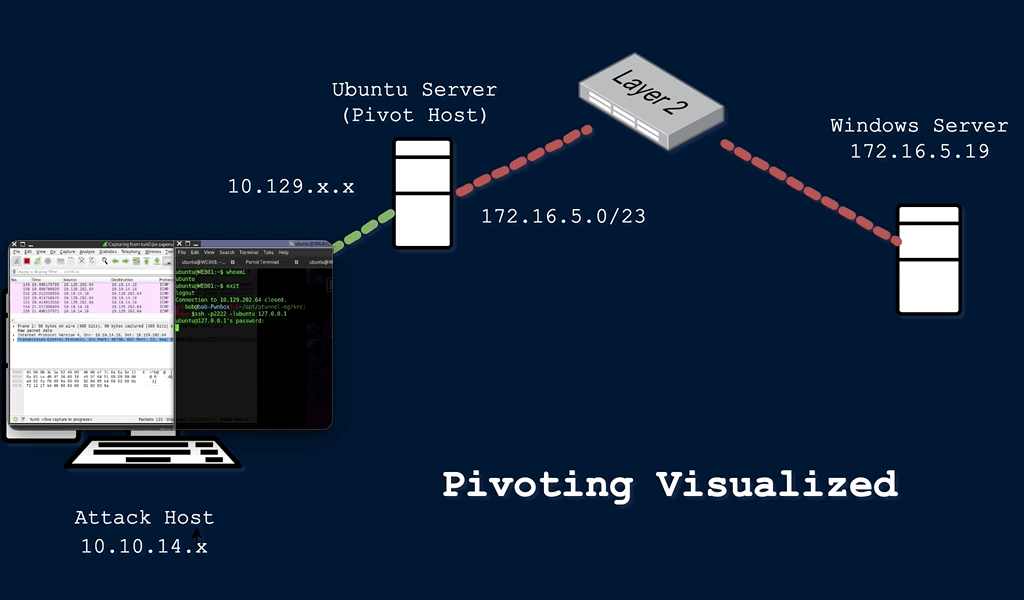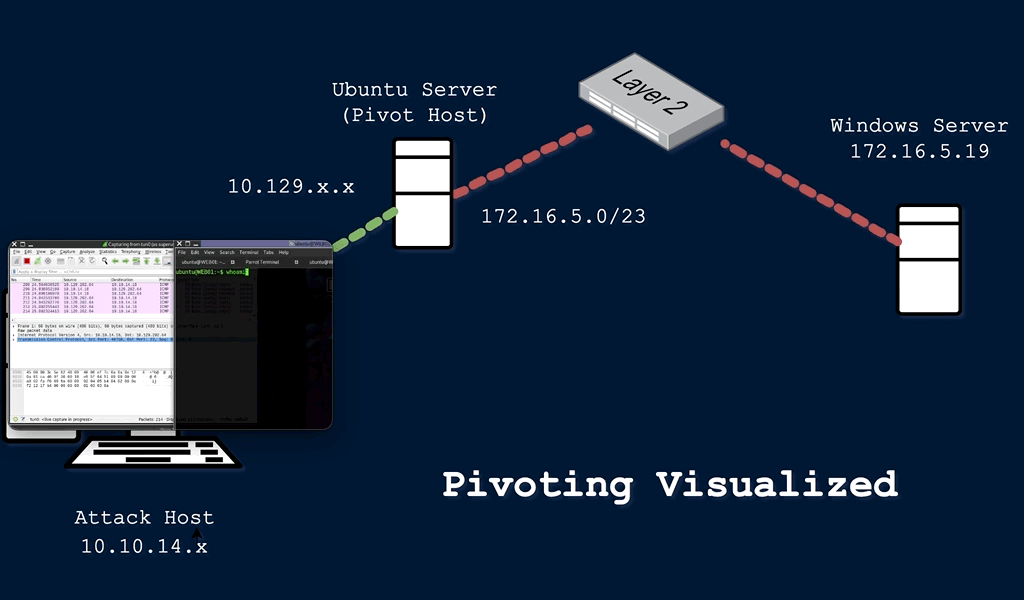
GitHub - dievus/ADGenerator: Active Directory Generator files for Movement, Pivoting, and Persistence for Pentesters and Ethical Hackers.

Active Directory Lab Setup - (Mayor's Movement, Pivoting & Persistence Course Walkthrough) | Oste's Blog

X \ TryHackMe على تويتر: "Introducting Holo, a network to teach you how to hack Windows Active Directory & more! 🔵 AV Evasion 🔵 Container Escapes 🔵 Active Directory Attacks & Pivoting
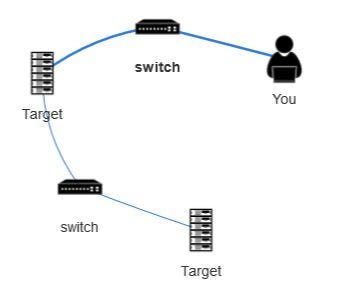
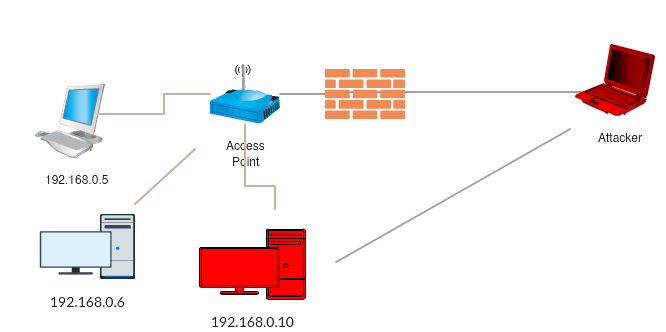
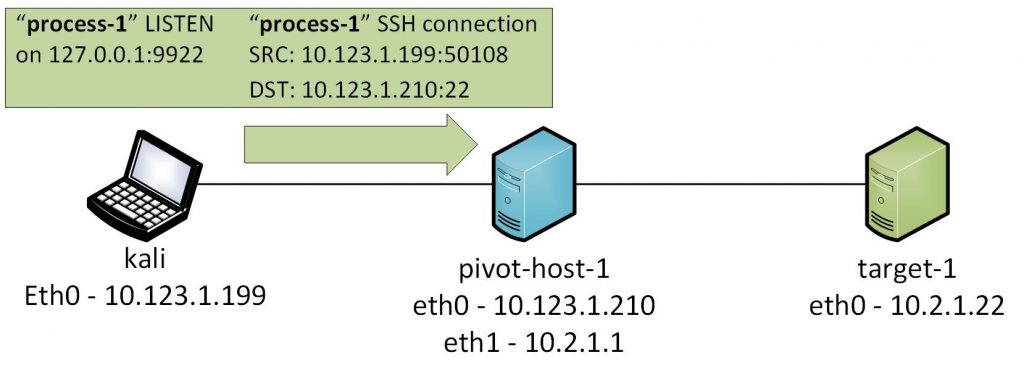
Basic Network Pivoting. Assalamualaikum | by Achmadinata | MII Cyber Security Consulting Services | Medium
Death from Above: Lateral Movement from Azure to On-Prem AD | by Andy Robbins | Posts By SpecterOps Team Members

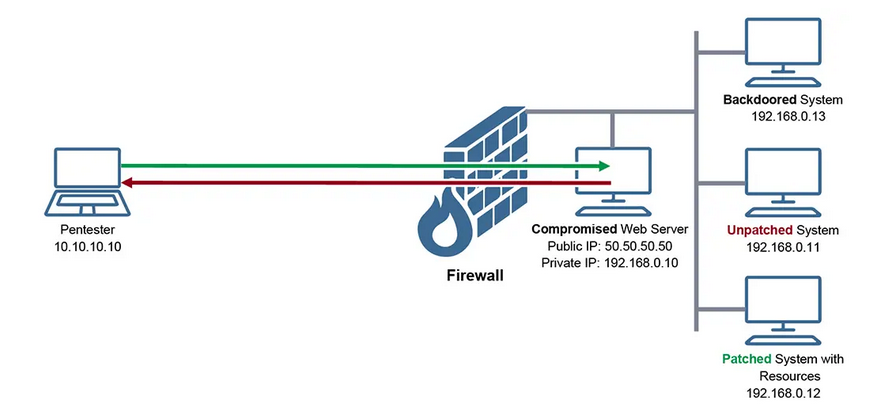

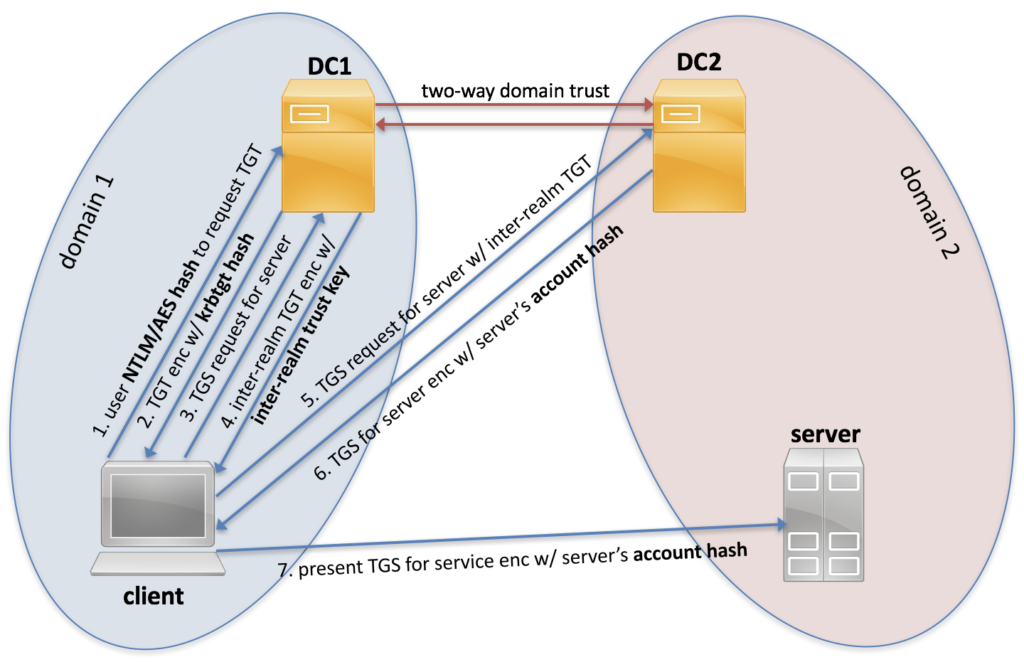

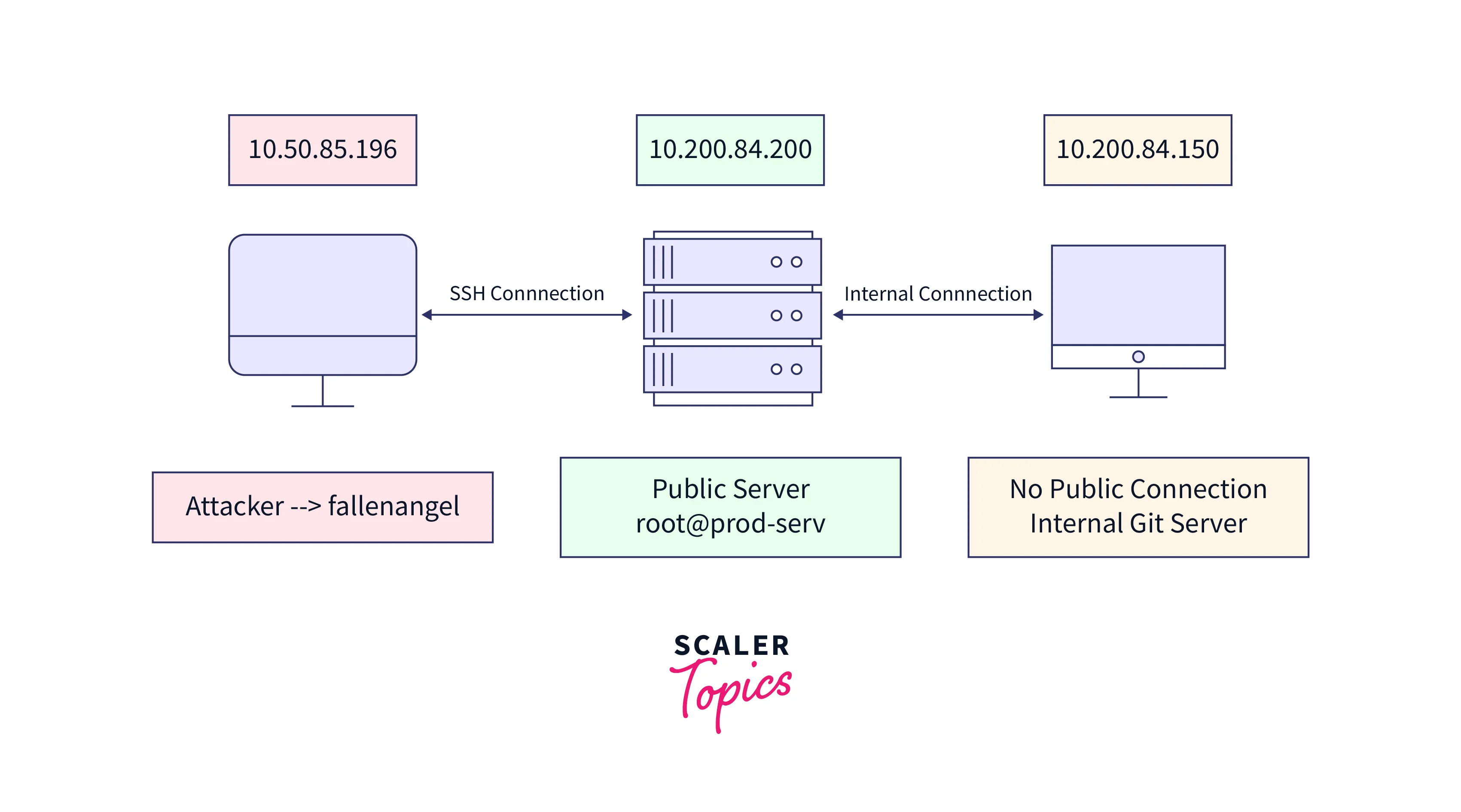
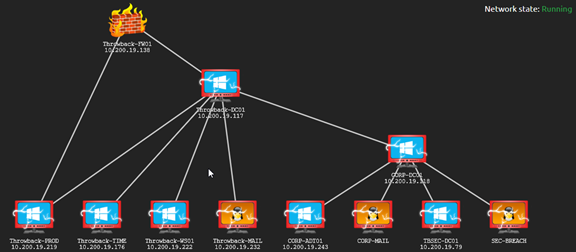




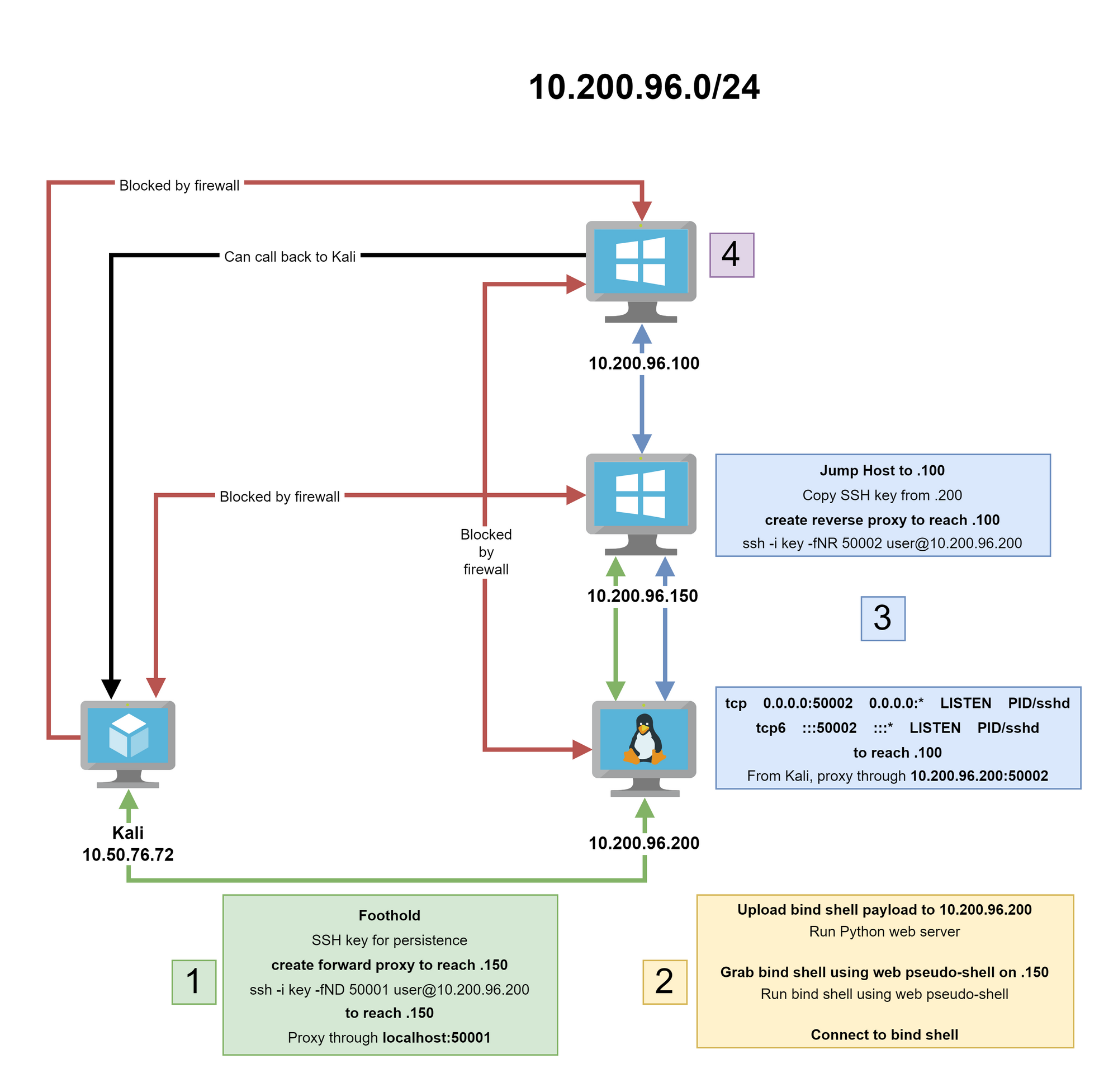



![Overview of network pivoting and tunneling [2023 updated] | Rawsec Overview of network pivoting and tunneling [2023 updated] | Rawsec](https://blog.raw.pm/images/pivoting/network1b.png)