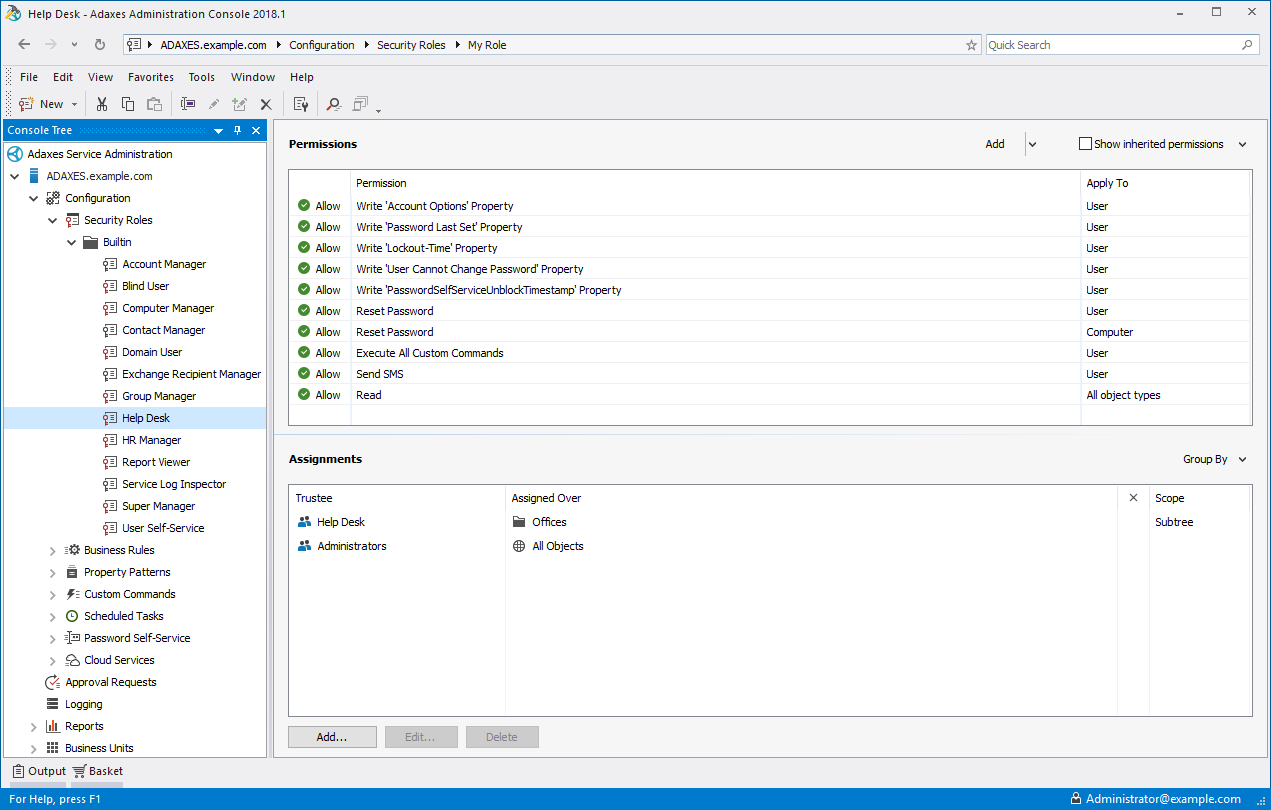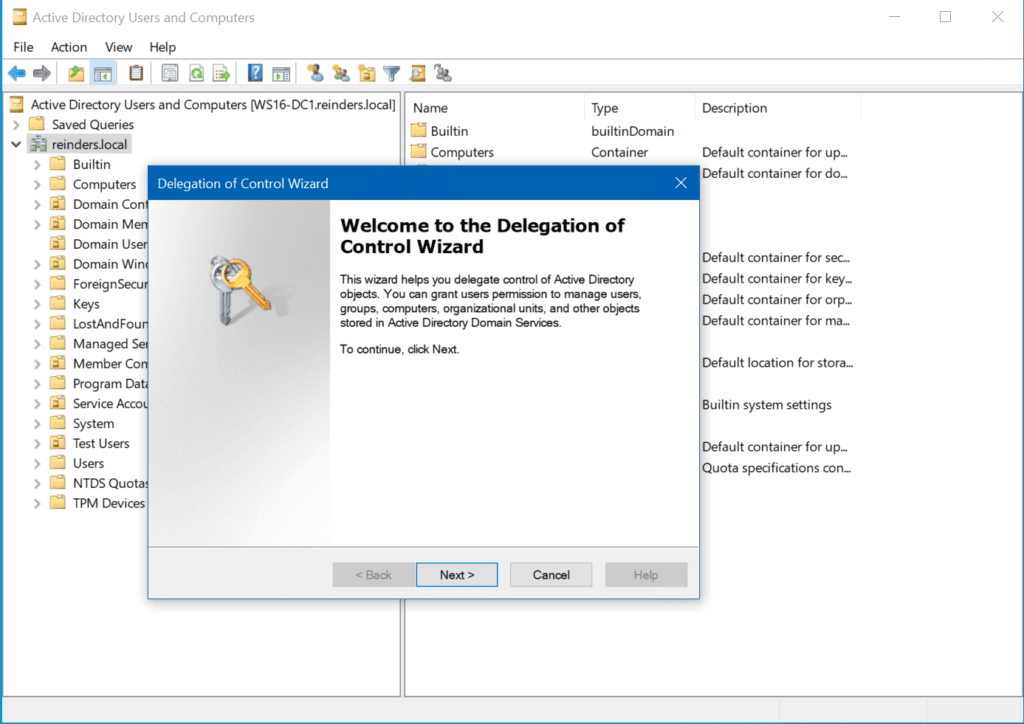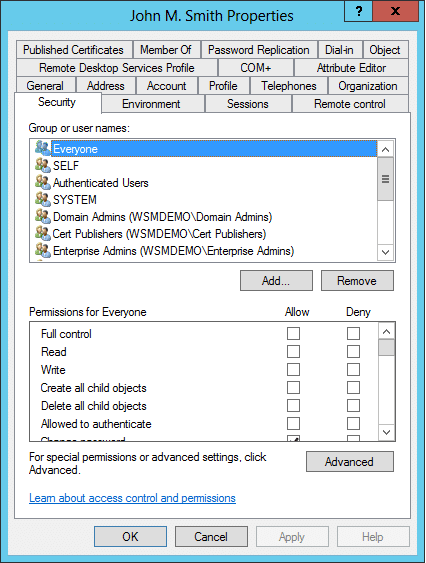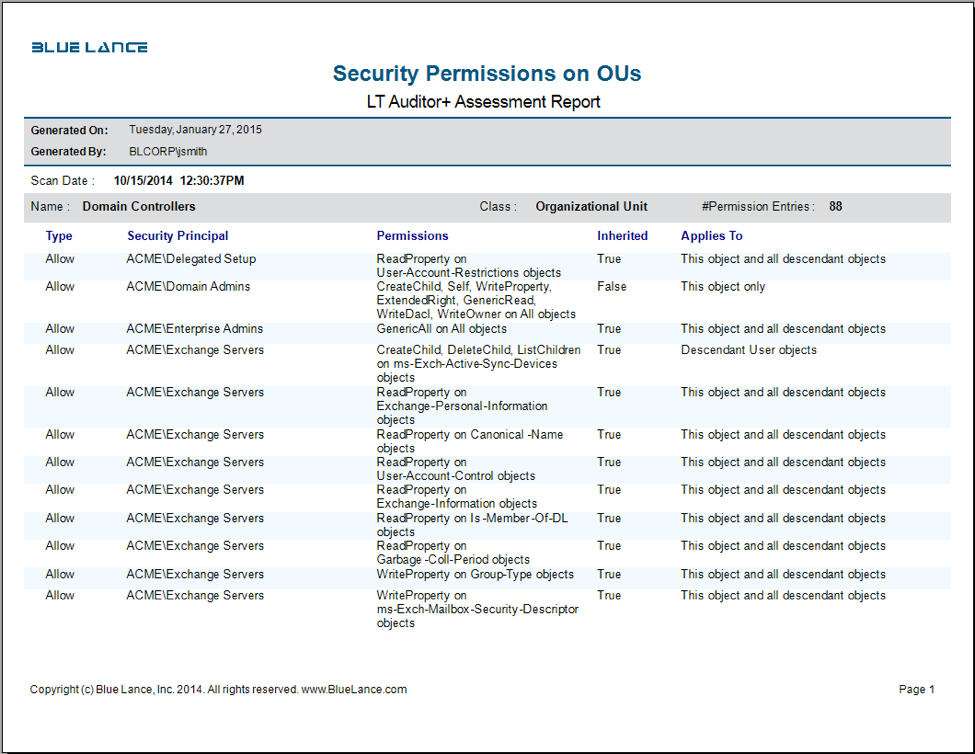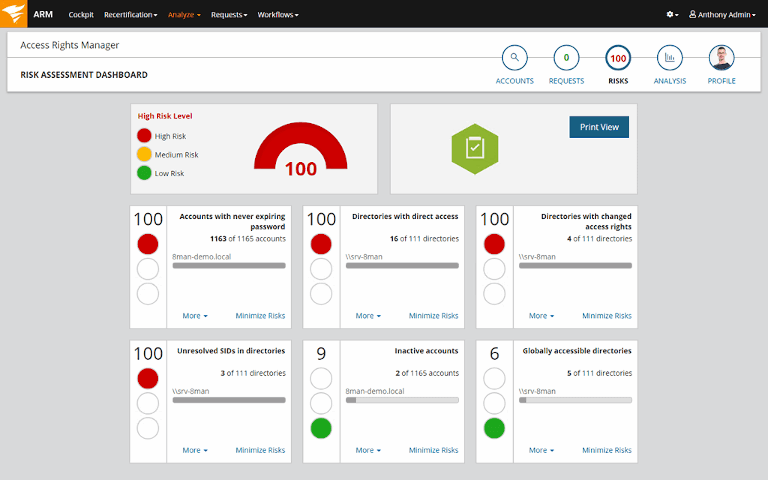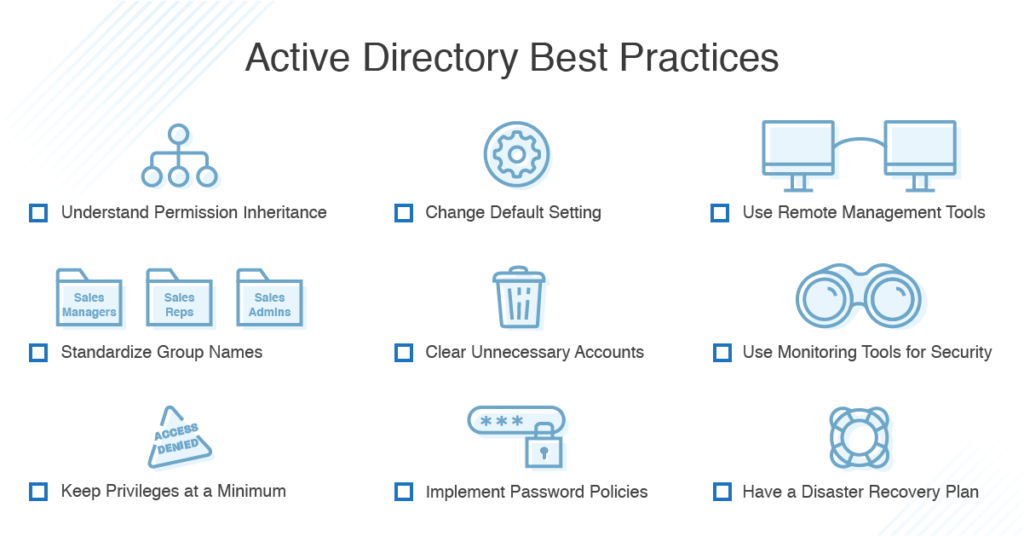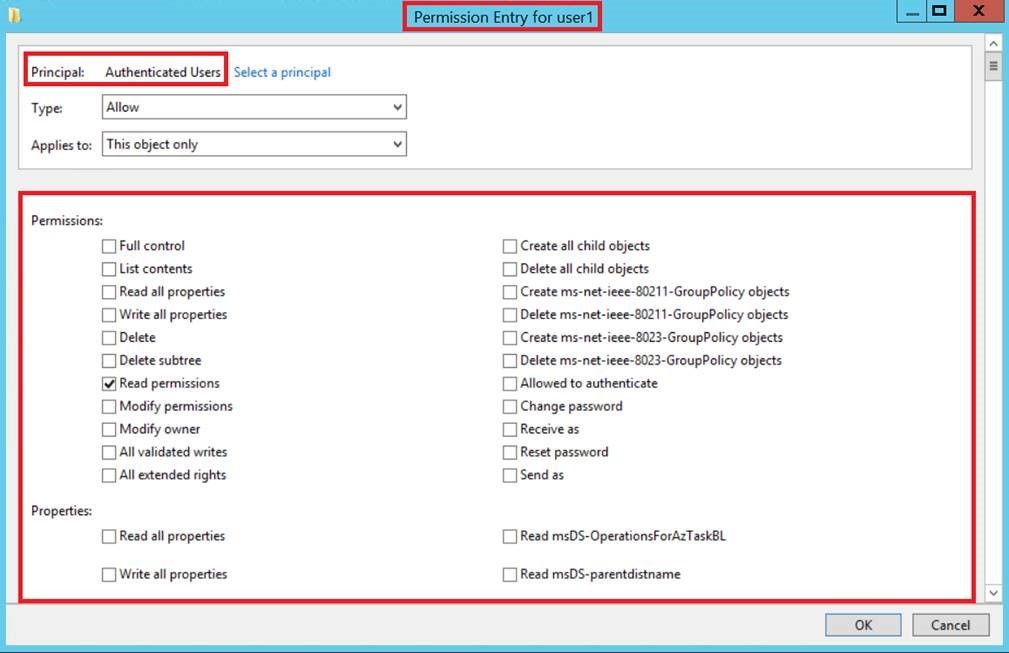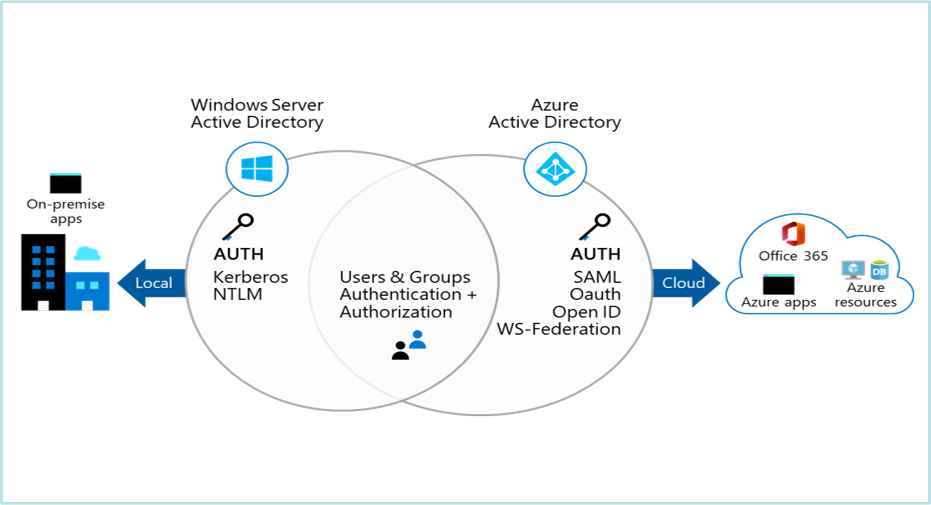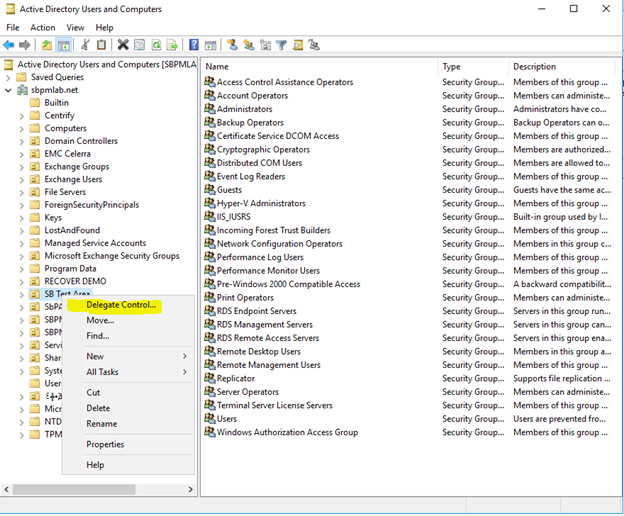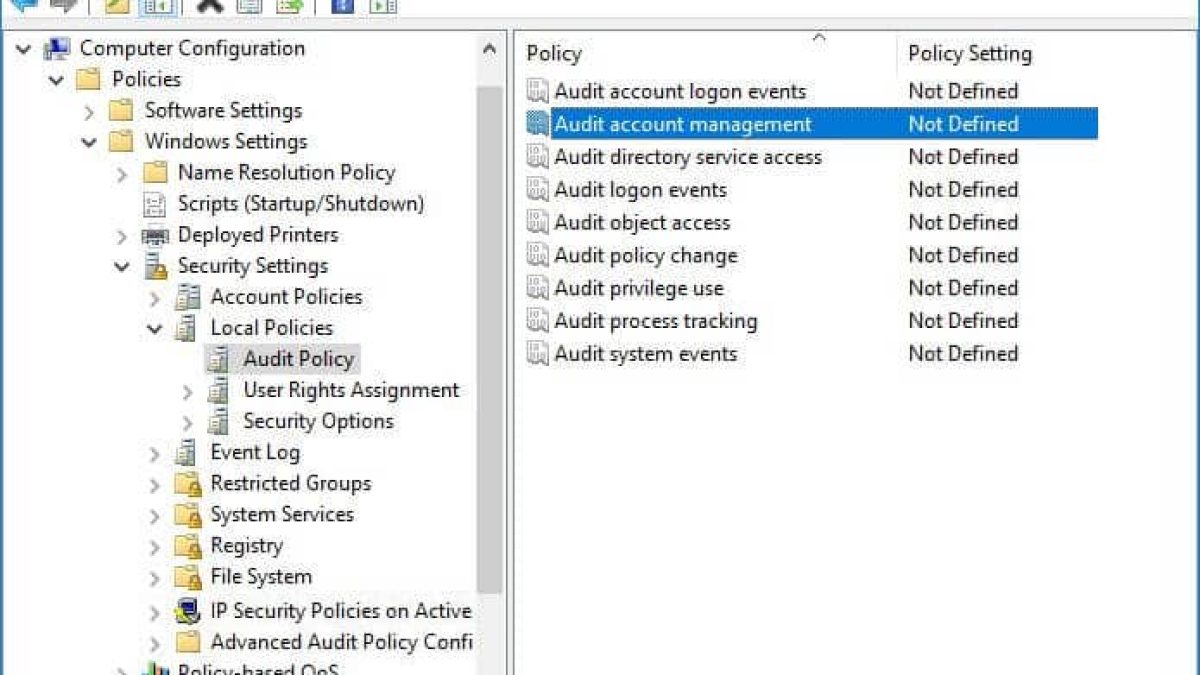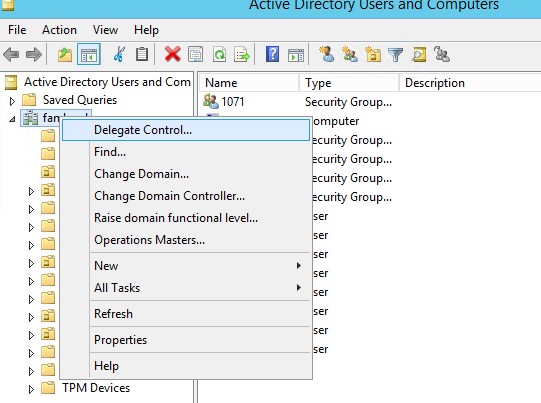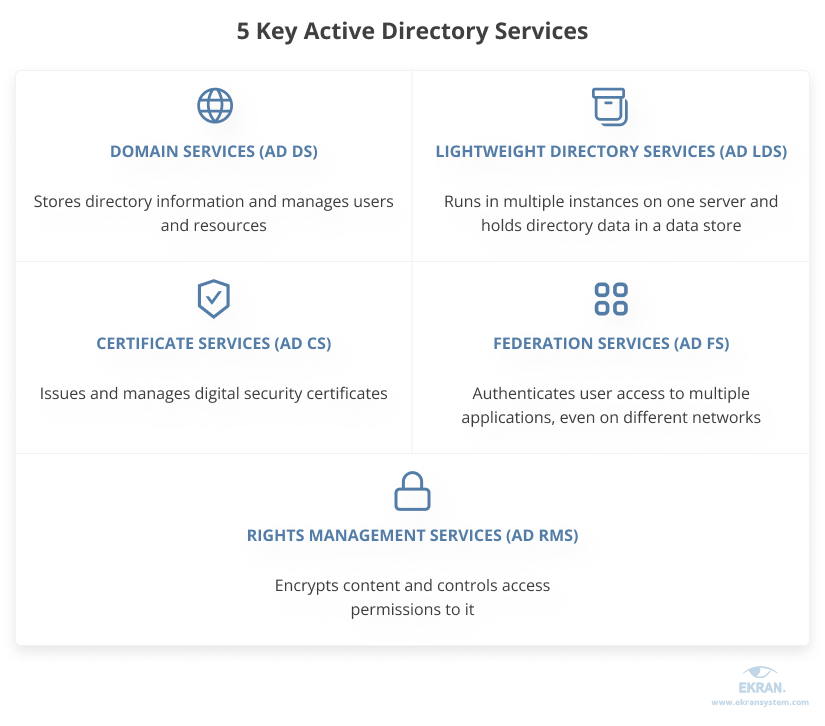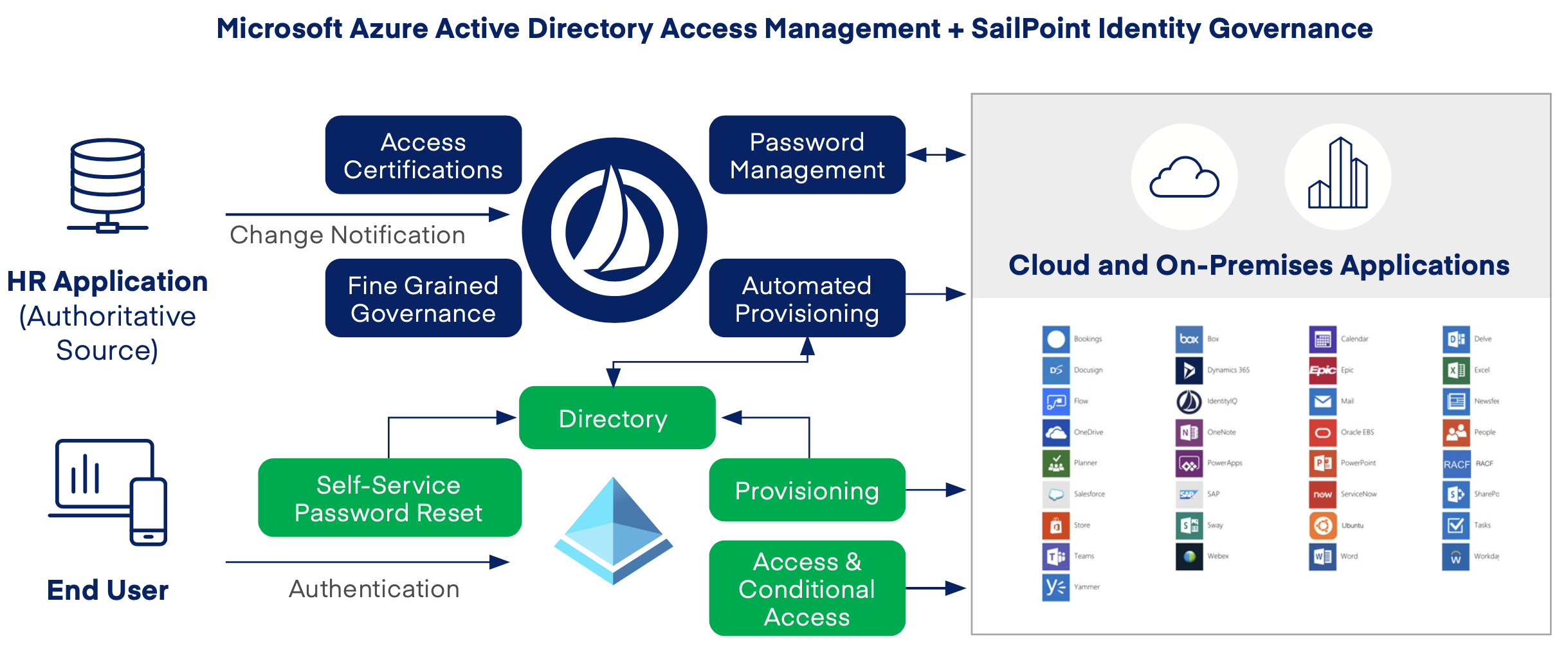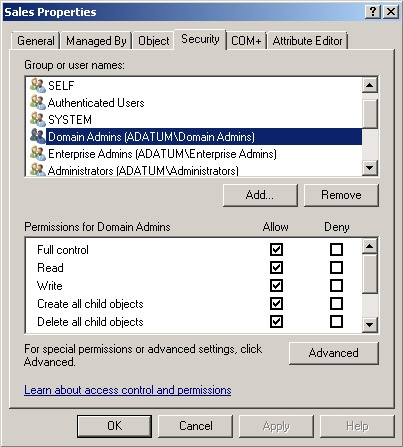
Delegating the Administration of Windows Server 2008 Active Directory Domain Services | Microsoft Press Store

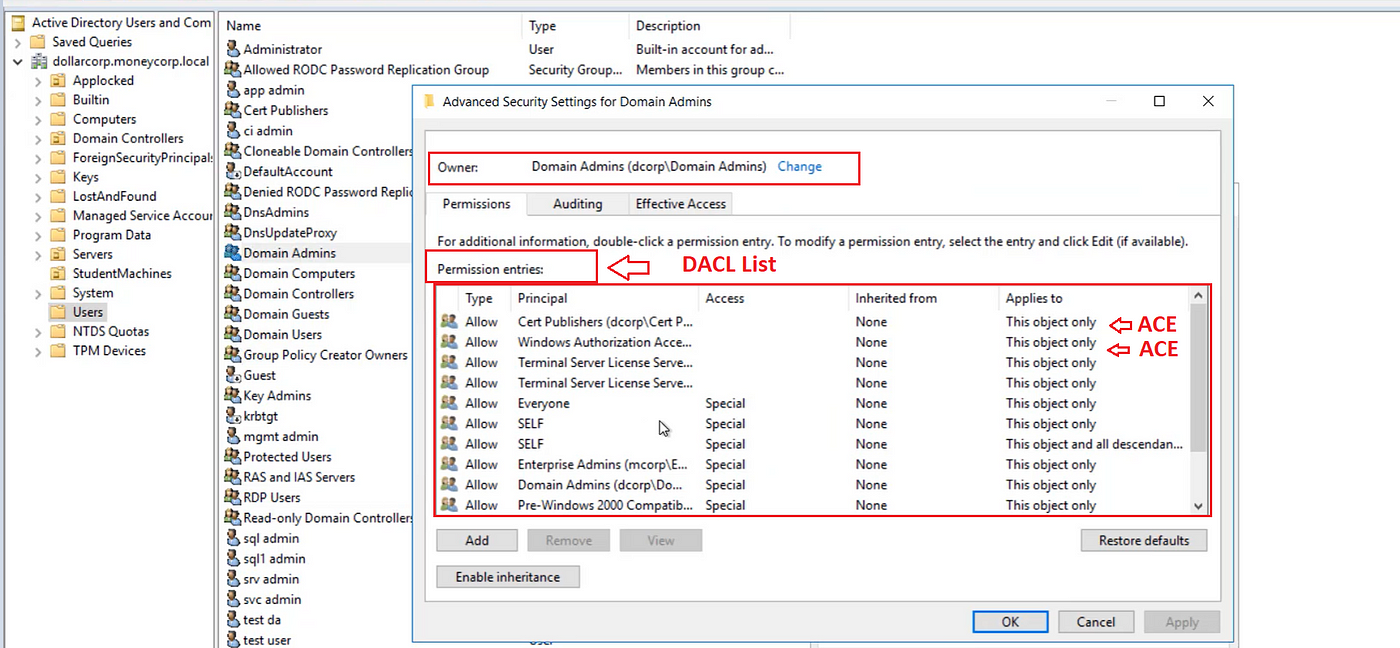
Active Directory Security Blog: Active Directory Effective Permissions - Paramount to Cyber Security

Active Directory Security Blog: Active Directory Access Control Lists (ACLs) - "Actual" Attack and Defense